What to look for when commissioning
Penetration test should pay attention
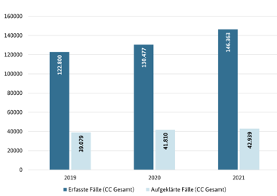
The threat posed by cybercriminals is steadily increasing in Germany. According to the annually published so-called Bundeslagebild Cybercrime of the Federal Criminal Police Office (BKA), the number of registered cases increased by over 12% percent to 146,363 last year. It should not go unmentioned here that the cases are increasing not only in quantity but also in quality. As a result, cybercriminals are becoming increasingly successful in penetrating even secure systems.
Cybercrime in the narrower sense is understood by the BKA to mean “criminal offenses directed against the Internet, information technology systems or their data.” These include, for example, attacks that lead to a deliberately induced overload of an institution’s or company’s network.
How can institutions or companies protect themselves from this? What role does penetration testing play in this and what should be considered when commissioning it?
Penetration tests (pentest for short) are security tests of individual computers or networks of any size. By auditing as many system components and applications of a network or software system as possible, security is put to the test to identify vulnerabilities. For this purpose, the same methods are used that a real attacker could use. This allows the sensitivity of a system to be simulated in a realistic scenario.
Penetration testing can:
- Uncover hidden security vulnerabilities before hackers do
- Save follow-up costs and reduce network downtime
- Supporting the development of efficient safety measures are
- Promote compliance with safety guidelines
- Preserve customer loyalty and the image of the company
- Evaluate the current IT security situation by an external third party (through an unbiased view with a different perspective on the system).
- Increase security at the technical and organizational level
- Detect potential errors (programming errors, logic errors, vulnerabilities)
Other advantages offered by a penetration test:
To understand the attacker, you have to act like a potential attacker. This approach gives a better overview of possible vulnerabilities and how an attacker would exploit them. This change in perspective is important in order to be able to clarify specific questions about the safety of the system. Penetration tests are also variable and versatile, e.g., to test a specific system component more explicitly. Equally well, these can be extended to include social engineering or physical tests, testing the security of office buildings and the previous competencies of employees for the topic of IT security.
Thus, there are many reasons why a pentest is needed. At first glance, one gets the impression that pentests only offer advantages to an organization, but what about possible disadvantages?
What disadvantages can a penetration test have?
If pentests are not performed professionally, major damage to your business can result.
For example, individual components or even the entire network may fail.
Furthermore, data loss can occur, e.g. by changing the database due to an ill-considered SQL query.
Furthermore, information about found vulnerabilities or other information that can form an attack vector can be leaked by attacking.
Therefore, it depends very much on which provider you choose. Because some companies sell under the term penetration test, security scans that do not correspond to the usual scope of a penetration test. This is often due to insufficient qualifications, cost savings or time savings, as penetration tests, as a rule, last for at least two weeks and are correspondingly time-consuming.
The bottom line of cons is to check the vendor to see if they offer qualified penetration testing. In order to pay attention to everything when commissioning, this aspect will be discussed in more detail in the next subsection. But before we turn to the final step, the commissioning, the question arises as to when and how often a pentest makes sense.
When is a penetration test useful?
In principle, a system can be tested at any time. However, it makes little sense for pentests to be performed repeatedly on an unchanged IT infrastructure. Therefore, we distinguish between a first-time, cyclic and minimal pentest.
Accordingly, we recommend different approaches:
First-time: If the pentest is being conducted for the first time, it must be done thoroughly to determine the current status quo of the organization. This means that all components of the IT infrastructure should be thoroughly examined and then well documented.
Cyclic: To be able to maintain the safety level, regular pentests are the best choice. This usually involves developing a dedicated penetration testing program with the IT security company. This program is regularly adapted to the situation, especially changes, of the organization. This ensures that all new features resulting from changes are sufficiently tested.
Minimal: Every organization should perform a detailed pentest on all components at least once a year in order to be able to make a good assessment of its own IT security situation.
In practice, it has proven effective to first perform a one-time pentest and then develop a cyclical penetration testing program. This keeps the security standards as high as possible and offers a potential attacker little to no attack vectors. The principle of testing and the timing of tests would thus be covered, but what must now be considered when commissioning?
What should you look for in the appointee?
Below are 5 points that organizations can use as a checklist when commissioning:
- Who do I hire to perform a penetration test?
Classically, IT security companies are a GmbH, AG or GmbH & Co KG. Exceptions prove the rule – but there are also some points where you should be suspicious:
- Is the IT security company a UG (limited liability)?
This is a very young company. A company that either was not prepared to make a capital contribution of 25,000 euros or was not yet able to do so. At this point, we recommend only commissioning small studies with a project volume of less than 10,000 euros.
- Is the IT security company insured?
Penetration testing can cause damage as listed above in the disadvantages. This can be mitigated by an adequately covering sum insured. Before commissioning, it should be estimated how much the damage could be and compared with the maximum sum insured.
- Are the persons responsible in the imprint individuals?
If the responsible person is an individual instead of a legal entity, we recommend that you refrain from commissioning the work. There is no way to prove the authenticity of a person. Caution is also advised in the case of GbR. There is no obligation to register!
- Is a sales tax identification number indicated in the imprint?
The missing Ust. Id. No. directly shows that the potential contractor has done very few, small projects in the last and current year. Commissioning should be avoided.
- Does the IT security company demonstrate demonstrable in-depth knowledge?
If the company is not demonstrably qualified, we advise against commissioning! Only those who can present the appropriate certificates (e.g. CSP, CEH, CISSP, OSCP, implementation concepts BSI/PTES/MITRE Attack Framework, etc.) can test properly according to certain standards.
- Is it a day-to-day business or one service out of many?
While large to very large IT service providers have the monetary and human resources to meet the demands of multiple core businesses, we recommend that small and medium sized companies be contracted to perform a penetration test. These usually offer greater flexibility, flat hierarchies and the possibility of speedy project completion.
You have found a company that has a suitable legal form and has the personnel as well as the expertise to perform a penetration test?
– now ask for a quote.
- Can the following questions be answered after receiving the offer?
- How many people will be involved in the project?
- What are the qualifications of the people involved?
- Is it tested according to international standards?
- What is the exact procedure for performing the penetration test?
- Does the contracted company have a static IP address?
Using a static IP address, not only can the client perform whitelisting, he can also see at a glance which attacks and tests the contractor is performing on his own infrastructure. In addition, whitelisting allows the client’s IT department to determine if detected attacks are part of the penetration test or if it is a real attack.
- Who is responsible for the penetration testing project?
A permanent contact person on the part of the contractor and the client is important for communication about the current status of the project. This minimizes the effort and number of meetings. Both contact persons thus exchange the necessary information and questions with each other and, if necessary, pass them on to your colleagues for clarification.
Conclusion
In summary, penetration testing is essential in today’s digital age! The number of cases recorded by the BKA’s Bundeslagebild Cybercrime (Federal Situation Report Cybercrime) is increasing annually, with the number of solved cases remaining more or less constant at 39,000 – 43,000. This means more and more cases cannot be solved. Thus, self-protection is required, in which penetration tests play a key role, as they significantly minimize the risk of being affected by cyberattacks. If you now commission a penetration test, taking into account the points described above, nothing should stand in the way of successfully conducting the pentest and improving your security level.